As digital infrastructures become the backbone of global economies, a transformative shift is underway. Quantum computing, once confined to theoretical physics, is now a rapidly emerging field poised to disrupt everything from artificial intelligence to cryptography.
Unlike classical computers, which operate on bits (1 or 0), quantum computers process information using qubits that can exist in multiple states simultaneously, which enables them to perform vast numbers of calculations in parallel.
While computing power accelerates, current encryption systems such as RSA and ECC, which secure everything from bank transfers to national defence infrastructure, face an existential threat. This is where Quantum Cryptography enters the conversation.
The Rise of Quantum Cryptography
Quantum Cryptography emerges not merely as a response to quantum computing but as a security framework inherently rooted in it. If quantum machines can break today’s encryption, then security must evolve to operate on the same principles.
Quantum Cryptography harnesses quantum mechanics to create security protocols that cannot be broken, even by a quantum computer. Its most well-known implementation, Quantum Key Distribution (QKD), ensures that any attempt to intercept or eavesdrop on communication changes the system and alerts users in real-time.
This approach is not based on mathematical assumptions but on the laws of physics, creating a new paradigm for digital trust.
Understanding the Fundamentals of Quantum Cryptography
At the heart of Quantum Cryptography lies the manipulation of quantum particles — primarily particles of light (photons) — to guarantee the confidentiality of data. Several fundamental principles underpin its operation:
- Quantum Superposition: In the quantum world, a particle can exist in multiple states at once until it is observed. This property allows the encoding of information in a way that cannot be precisely duplicated.
- Quantum Entanglement: When two particles become entangled, they maintain a connection no matter the distance between them. Changes to one particle instantly affect the other, offering new pathways for ultra-secure communications.
- Quantum Measurement: Observing or measuring a quantum system alters its state, destroying the particle’s superposition and forcing it to become either 0 or 1, an effect that acts as an automatic intrusion detection system in a quantum network.
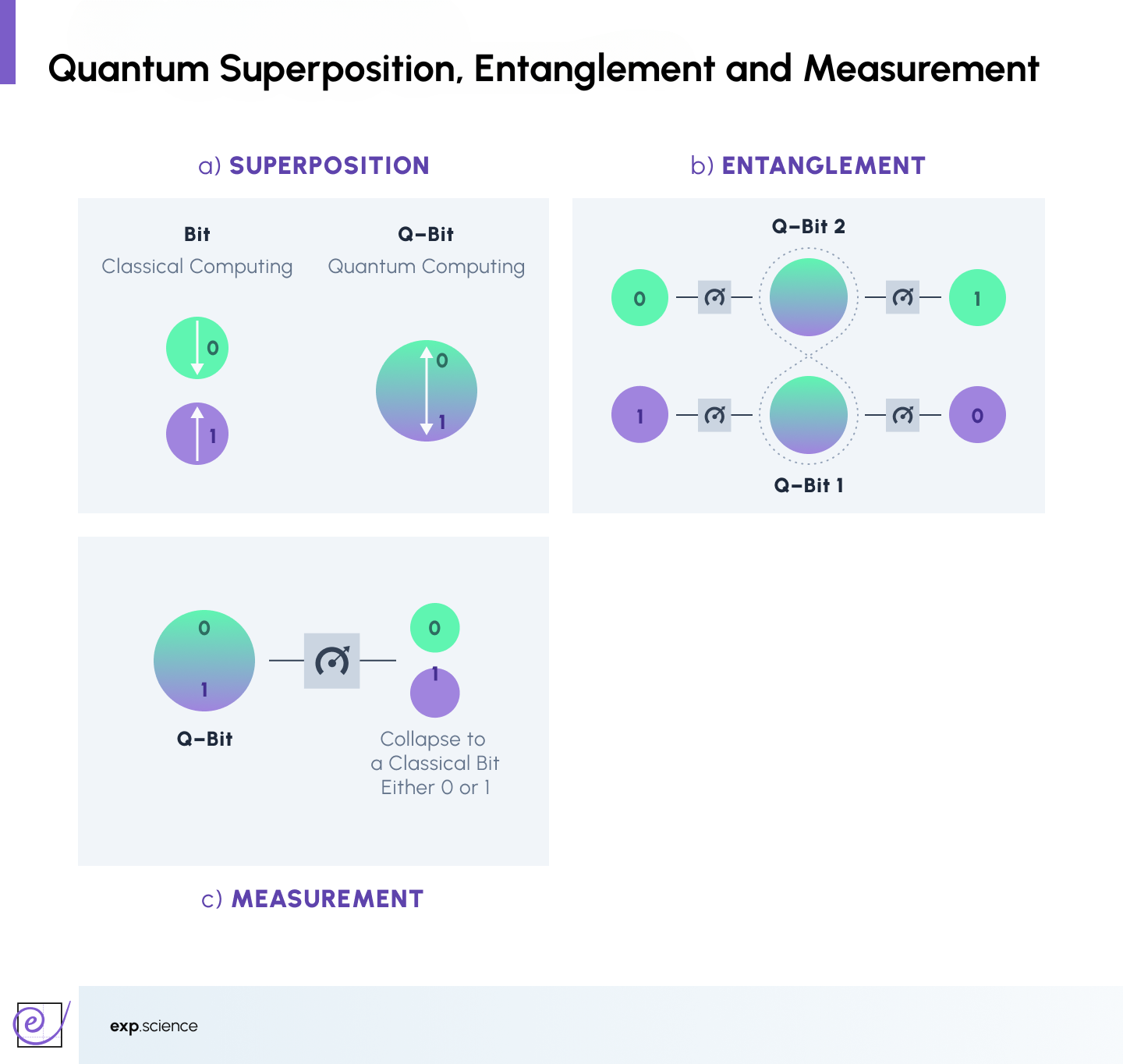
These phenomena are exploited through methods such as Quantum Key Distribution (QKD), which enables two parties to create a shared secret key for encryption, guaranteeing that any eavesdropping attempt would be immediately noticed.
What Is Quantum Key Distribution (QKD)?
Quantum Key Distribution is the flagship application of Quantum Cryptography. The BB84 protocol, introduced by Charles Bennett and Gilles Brassard in 1984, remains the most renowned QKD method. It enables two parties to exchange a secure encryption key using photons. If an attacker tries to intercept the transmission, their actions will disturb the photons' quantum states, signalling the intrusion.
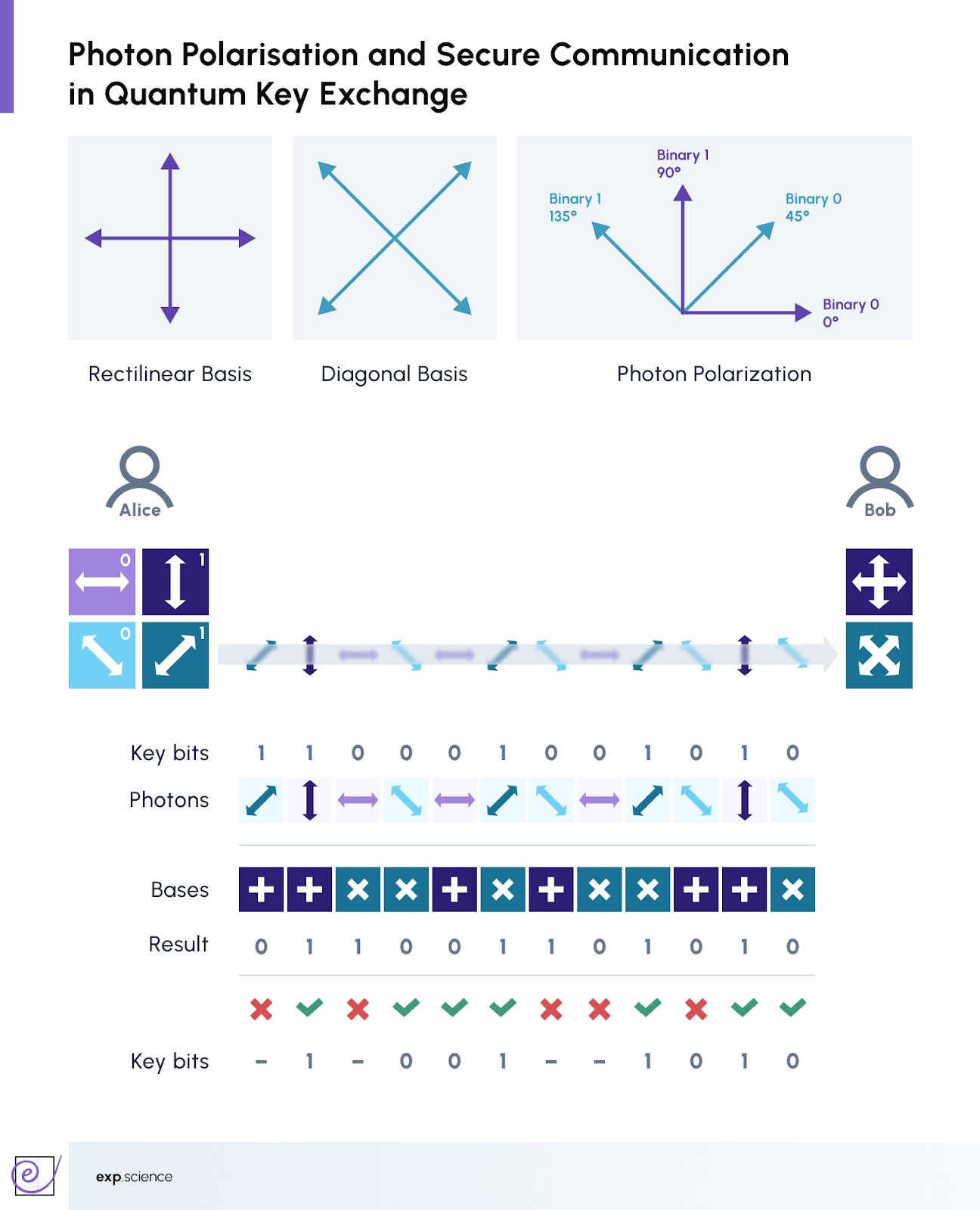
The principles of photon polarisation, shown using rectilinear and diagonal bases, underpin the quantum key exchange between Alice and Bob, where each photon's polarisation encodes key bits. The visual illustrates how photon states and measurement choices affect the security of the shared secret. Below is a simplified overview of how QKD works:
- Key Generation: Alice sends Bob a series of photons encoded in random quantum states.
- Key Sifting: Bob measures the incoming photons, choosing random measurement bases.
- Key Comparison: They compare a portion of their results over a classical channel to identify matching bits.
- Key Distillation: Errors are corrected, and privacy amplification is used to ensure the key’s secrecy.
Considering that any interception attempt inevitably disturbs the quantum states, QKD enables truly secure communication channels.
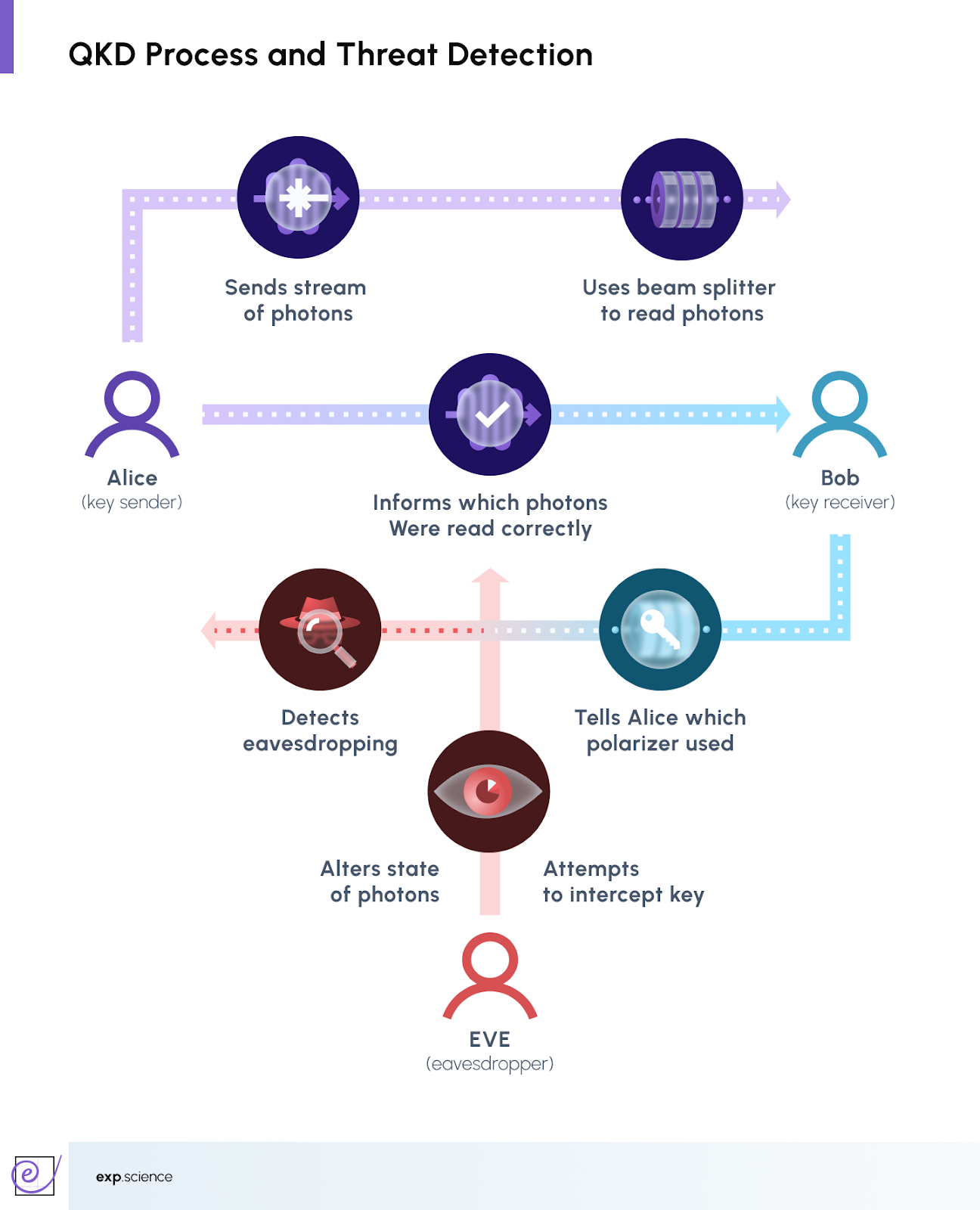
A simplified walkthrough of Quantum Key Distribution (QKD), highlighting the secure exchange between sender (Alice) and receiver (Bob), and the role of an eavesdropper (Eve), whose interference disrupts photon states and triggers an alert. Additionally, more advanced QKD protocols are being explored, including:
- E91 Protocol: Based on quantum entanglement, offering even higher resilience to attacks.
- Measurement-Device-Independent QKD (MDI-QKD): Designed to remove vulnerabilities associated with detector hacking.
The innovation within QKD ensures that Quantum Cryptography remains a highly active area of research and development.
Real-World Applications and Deployment of Quantum Cryptography
As research matures, Quantum Cryptography is moving into tangible, real-world applications. Several high-profile projects showcase its growing relevance:
- China’s Micius Satellite: In 2017, China demonstrated the world’s first intercontinental quantum-secured video call between Beijing and Vienna using the Micius quantum satellite.
- BT and Toshiba Trials: British Telecom and Toshiba collaborated on a QKD-secured network in the United Kingdom, demonstrating use cases in financial services and critical infrastructure.
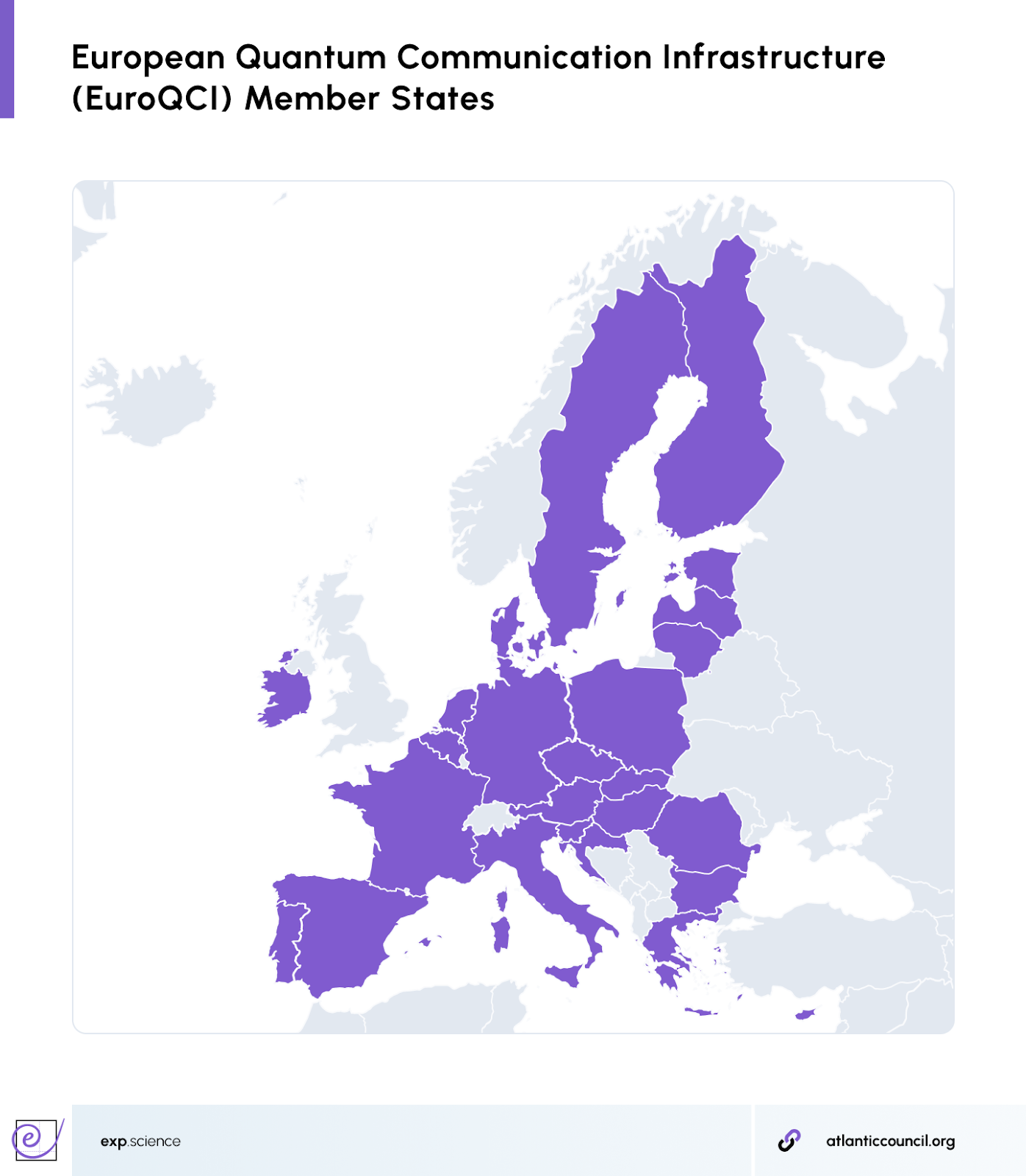
- European Quantum Communication Infrastructure (EuroQCI): A European Commission project aiming to create a secure quantum communication backbone across the European Union by 2027.
- Hedera and SEALSQ Chips: Decentralised network, Hedera, and the semiconductor firm SEALSQ are co-developing quantum-resistant secure chips to protect blockchain transactions and other critical infrastructure against future quantum-computer attacks.
In the private sector, financial institutions, governments, and healthcare providers are exploring how Quantum Cryptography can protect everything from transactions to confidential patient data. The technology is proving particularly relevant in domains where data sensitivity and long-term confidentiality are critical, including banking, defence, healthcare, and telecommunications.
Leading technology firms, such as IBM and Google, are also investing heavily in quantum research, highlighting the industry’s commitment and interest in the field. For instance, IBM recently announced a $150 billion investment plan over five years, with over $30 billion specifically for R&D in mainframe and quantum computers, bolstering its IBM Quantum program efforts in quantum-safe cryptography.
Meanwhile, Google continues its significant investments through its Quantum AI campus, notably developing advanced processors like "Willow" to enhance quantum error correction and backing diverse quantum technologies, as seen in its investment in neutral atom quantum computing pioneer QuEra Computing.
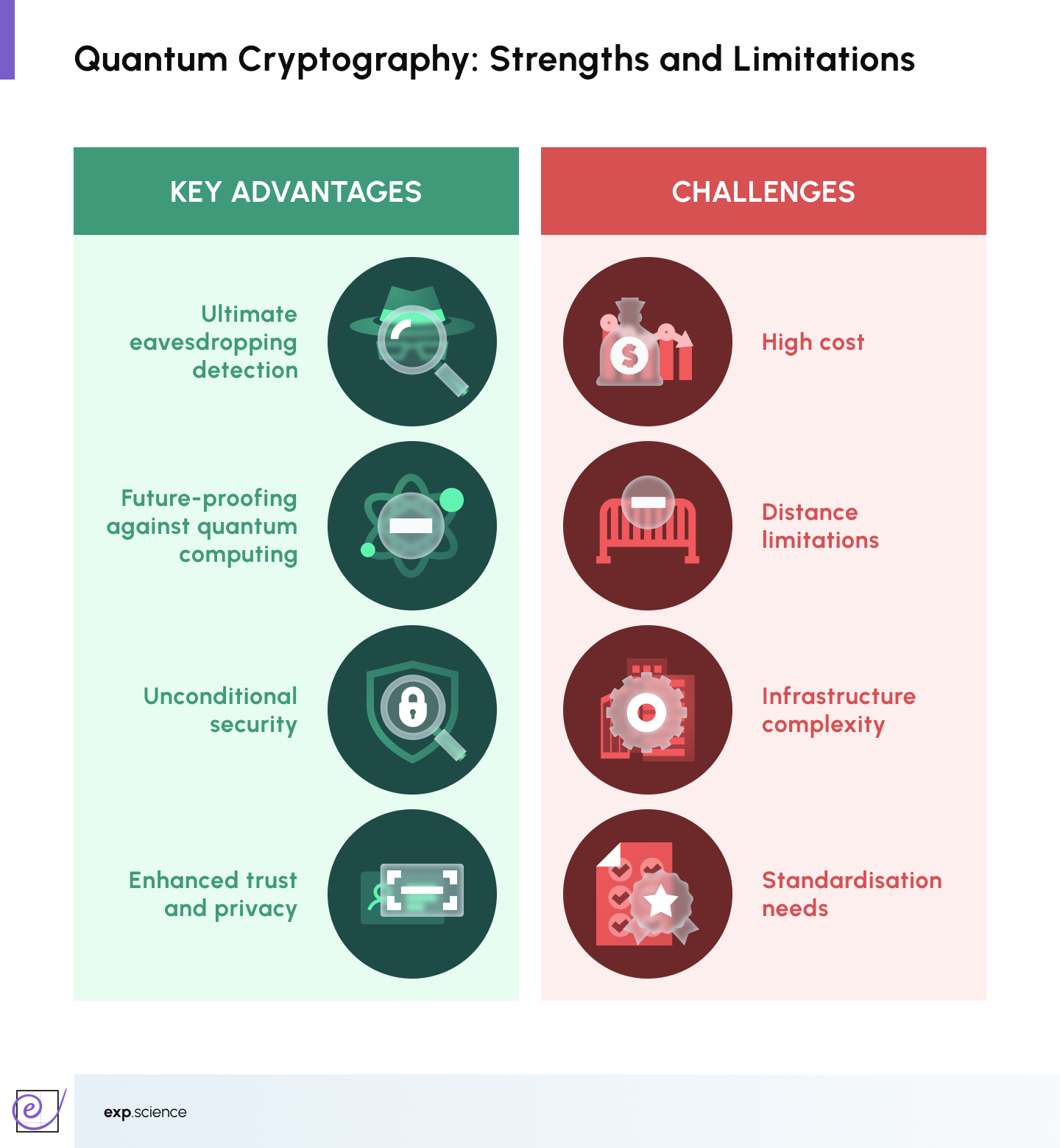
Key Advantages of Quantum Cryptography
Quantum Cryptography offers transformative advantages compared to classical encryption technologies:
- Ultimate Eavesdropping Detection: Any interception attempt disrupts quantum states, alerting users instantly.
- Future-Proofing Against Quantum Computing: Classical encryption may be broken by quantum computers; Quantum Cryptography remains secure.
- Unconditional Security: Based on the immutable laws of physics rather than computational assumptions.
- Enhanced Trust and Privacy: Offers a trustless system where the physics itself guarantees integrity.
Challenges Facing Quantum Cryptography
Despite its promising potential, Quantum Cryptography still faces notable challenges:
- High Cost: Quantum communication equipment, such as photon detectors and quantum repeaters, remains prohibitively expensive for widespread adoption.
- Distance Limitations: Current QKD systems struggle to transmit over long distances without the use of trusted repeaters or satellites.
- Infrastructure Complexity: Deploying quantum networks requires significant upgrades to existing communications infrastructure.
- Standardisation Needs: There is a need for international standards and regulatory frameworks to ensure interoperability and trust.
While quantum protocols, such as QKD, offer theoretically unbreakable encryption, some researchers have identified vulnerabilities not in the quantum systems themselves but in their physical implementation. One of the main concerns is the risk of side-channel attacks, which exploit hardware-level flaws, such as detector behaviour, to undermine communication security, as demonstrated in experiments by teams at the National University of Singapore who have been exploring solutions to this flaw, including optical power limiters and verification protocols.
On the other hand, several institutions are developing innovative solutions to address broader limitations. According to the Quantum Internet Alliance, one of the most promising development paths involves Quantum Repeaters and Trusted Node Networks, designed to overcome photon loss and securely transmit quantum keys over long distances. Meanwhile, agencies like NASA are testing satellite-based quantum communication systems aboard the International Space Station, laying the groundwork for a global quantum internet.
Quantum Cryptography Versus Post-Quantum Cryptography
It is important to distinguish between Quantum Cryptography and Post-Quantum Cryptography. Although both aim to secure information in a world with quantum computers, their approaches differ:
- Post-Quantum Cryptography: Relies on classical algorithms designed to be resistant to quantum attacks, using mathematical structures such as lattice-based cryptography.
- Quantum Cryptography: Utilises the fundamental laws of quantum physics itself to secure communications.
While post-quantum algorithms offer a quicker pathway to resilience with existing infrastructure, Quantum Cryptography provides long-term, physics-based security guarantees. Both approaches are likely to coexist as part of a layered security strategy in the coming decades.
The Convergence with Artificial Intelligence
Quantum technologies do not exist in isolation. They are converging with other transformative fields, most notably artificial intelligence. As mentioned by Berenice Baker, editor of Enter Quantum, in an IOT World Today note:
‘The convergence of quantum computing and artificial intelligence (AI) is poised to redefine the technological landscape in 2025… The integration of AI’s unparalleled efficiency and adaptability with quantum computing’s paradigm-shifting power offers a glimpse into a future where computational possibilities expand exponentially.’
AI, in turn, helps optimise quantum algorithms and hardware through error correction, noise analysis, and control system calibration. This symbiotic relationship is giving rise to Quantum AI — a new class of applications where AI systems are trained and deployed with the computational advantage of quantum architectures.
Explore: Blockchain, AI and Sustainability: How Emerging Technologies Converge
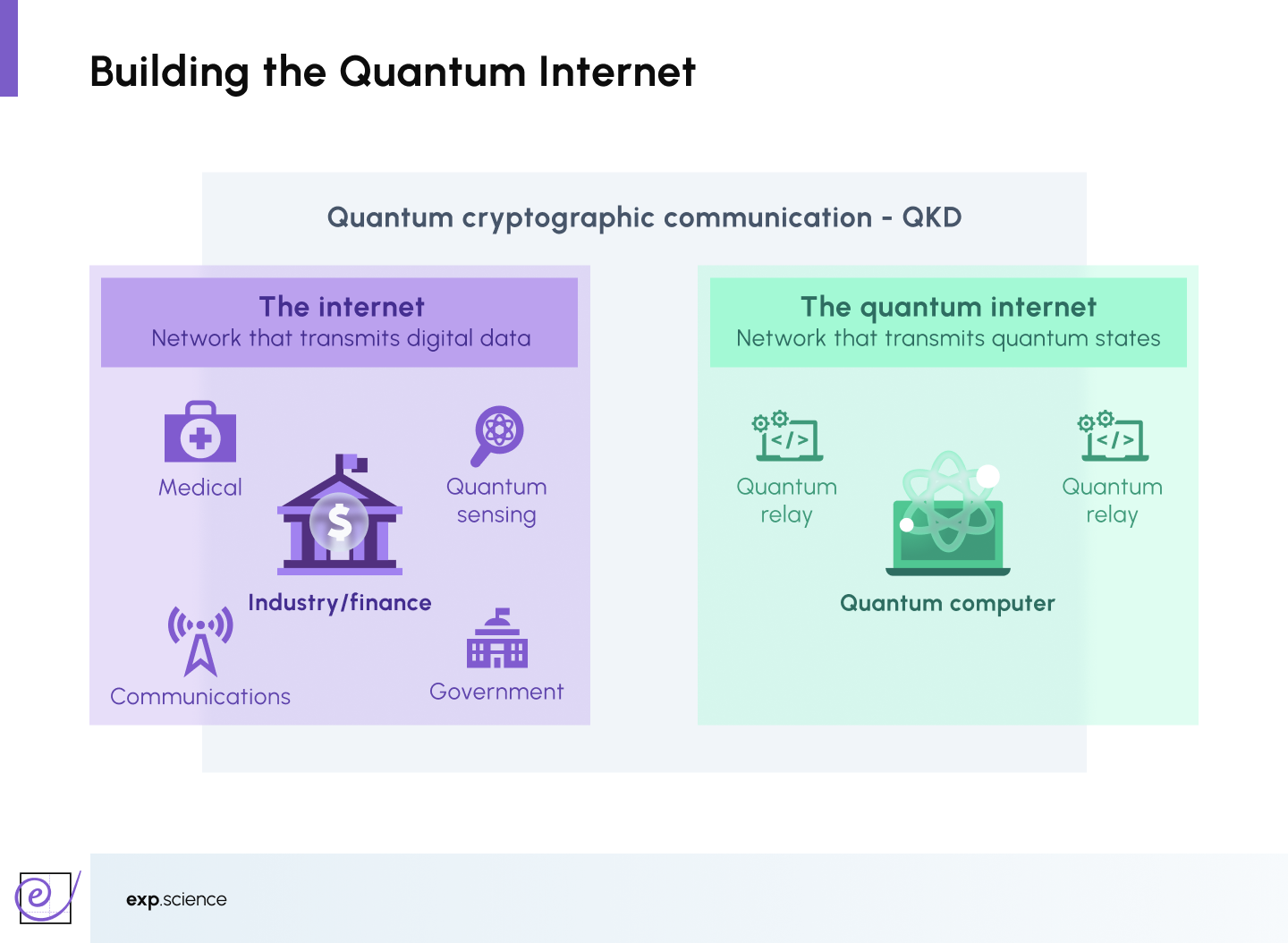
Towards a Quantum Internet
The long-term vision for Quantum Cryptography extends beyond secure point-to-point communication into the broader framework of the quantum internet, an infrastructure designed to transmit quantum states, rather than just classical digital data.
Quantum internet systems will operate in parallel with the classical internet, building on existing communication infrastructure while integrating quantum-specific components such as quantum relays, entangled photon sources, and secure quantum sensing mechanisms. This layered architecture will unlock entirely new capabilities that classical networks cannot support, including:
- Distributed quantum computing
- Ultra-secure voting and identity authentication
- Quantum-enhanced sensing applications
- Instantaneous and secure sharing of quantum information
Pilot projects in the Netherlands, China, and the United States have already demonstrated small-scale quantum networks, marking the early stages of a global shift towards quantum-secure infrastructure. In Europe, the Quantum Internet Alliance, led by Delft University of Technology, aims to deliver the continent’s first functional prototype of a quantum internet before the end of the decade.
As quantum communication technology matures, it is expected to fundamentally reshape digital trust, ushering in a new era of secure, decentralised, high-speed communications across sectors and borders.
Looking Ahead: Quantum Technologies and Data Ubiquity
When quantum technologies mature, their impact will extend beyond cryptography. A broader transformation is unfolding — one that will embed data and intelligence into every layer of infrastructure. According to a McKinsey article, authored by Asin Tavakoli and others:
“By 2030, many companies will be approaching ‘data ubiquity.’ Quantum-sensing technologies, for example, will generate more precise, real-time data… which applied-AI capabilities will be able to analyse to then recommend and make targeted software updates.”
The convergence of Quantum Cryptography, AI, IoT and sensing technologies will drive a new era of intelligent, responsive systems — from medical diagnostics to urban mobility and decentralised governance.


.jpg)

.jpg)
.jpg)
.webp)

