Digital identity (DiD) is a virtual representation of an individual, a device or an organization, used to identify, authenticate, and authorize their online activities. Digital identities are becoming more prevalent in an increasingly digital world, where identity serves as the gateway to unlocking services, verifying credentials and asserting rights. From accessing bank accounts to obtaining healthcare, DiD systems are the backbone of modern societal interactions.
However, conventional identity models are often centralised, siloed, opaque and prone to misuse; age-old credentials rest in government and platform silos, vulnerable to breaches and consent erosion.
According to World Bank ID4D data, approximately 850 million people worldwide lack formal legal identification, and over 3.3 billion have no recorded digital identity, excluding them from basic public services, financial inclusion and digital participation. This stark reality elevates digital identity beyond a mere technical consideration; it becomes a matter of human rights, access and trust.
As our lives shift online, questions around privacy, control, and inclusivity are growing louder and here is where digital identities can step in to help those stuck in the past leap ahead.
What Is a Digital Identity?
A digital identity is more than a login or a record; it encompasses all the data, attributes and credentials that represent a person, organisation or device in the online domain. These elements include:
- Core identifiers: such as name, date of birth and government-issued numbers.
- Authentication factors: like passwords, PINs, or biometric identifiers.
- Behavioural patterns: including online activity, location and device signatures.
When aggregated and verified, these datasets form a digital footprint that software and institutions use to securely authenticate and authorise users, detect fraud in real-time, and build trust across digital interactions.
Modern systems often rely on intermediaries, social media platforms and government databases, that gather extensive user data, often through opaque surveillance and algorithmic monitoring, limiting individual autonomy and concentrating exposure. Biometric systems, such as fingerprint or facial recognition, offer convenience and strong assurance, but the data is irrevocable if compromised, raising concerns about permanence and misuse.
Consequently, users often lack control over how personal data flows between issuers, service providers and aggregators, fuelling risks of mass surveillance, data monetisation and ongoing erosion of privacy.
Identity Models: Centralised vs Decentralised
Identity systems can be classified into three primary architectural models, each offering different trade-offs.
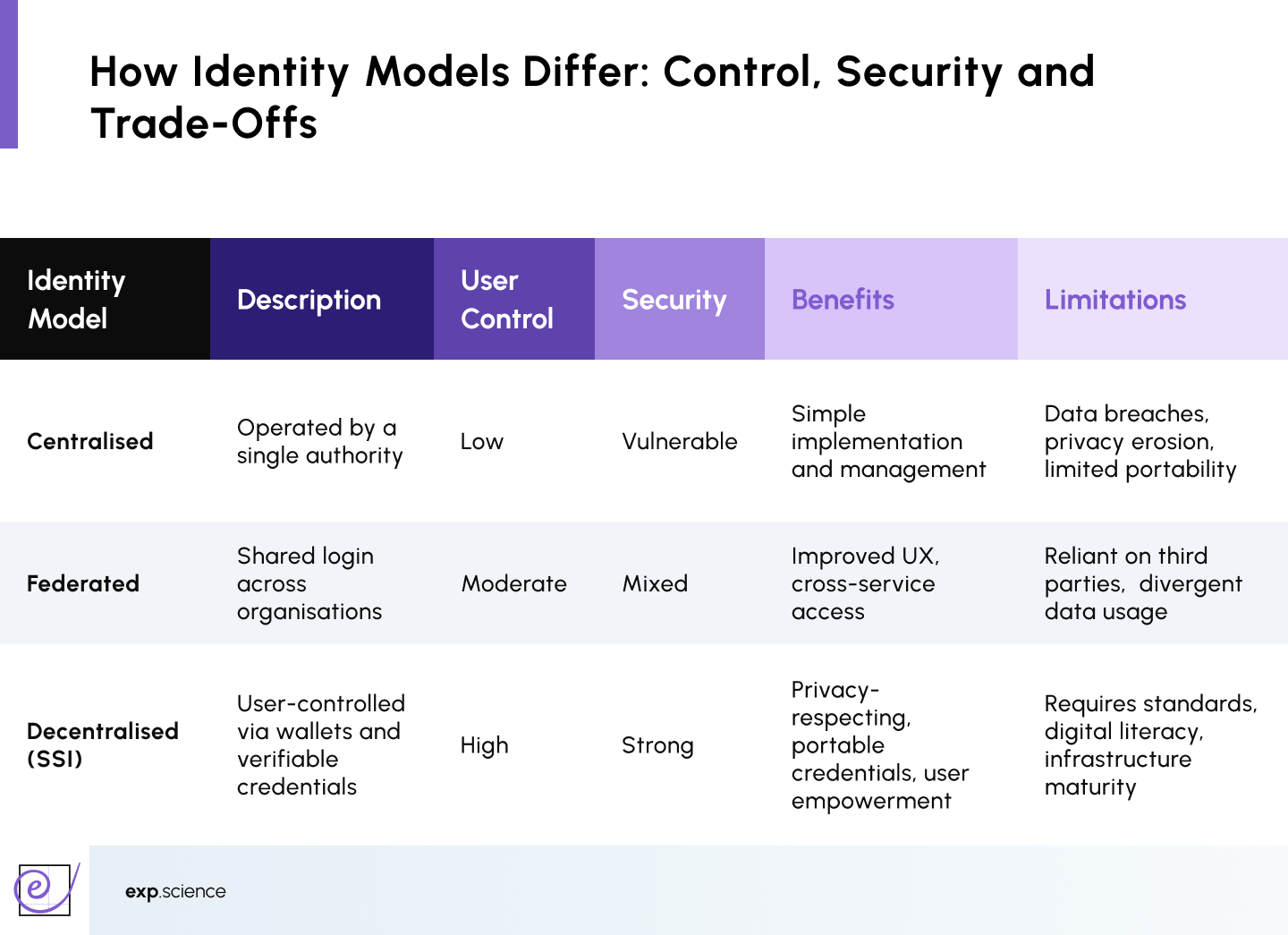
Centralised systems are currently dominant but have repeatedly failed, with examples like Equifax (147 million records) highlighting risks from large-scale data breaches. Meanwhile, federated systems, as demonstrated by the Facebook–Cambridge Analytica case (87 million users), reveal critical flaws in user control and reliance, exposing personal data to misuse.
While federated models improve UX and add flexibility, they still rely on central intermediaries. In contrast, SSI brings distinct advantages in terms of control and privacy but requires standards, digital literacy and infrastructure maturity.
Problems with Centralised and Federated Identity Systems
Both centralised and federated models concentrate control and data in the hands of a few actors, leading to a range of structural flaws:
- Privacy Risks: Centralised data repositories are prime targets for hacks. Incidents like the aforementioned Equifax breach or Cambridge Analytica scandal have already affected hundreds of millions, underscoring the scale and urgency of these risks.
- Lack of Interoperability: Incompatible identity silos force users to maintain multiple credentials and obstruct seamless digital ecosystems. Efforts such as the World Wide Web Consortium (W3C)’s DID/VC aim to standardise cryptographic identity formats to tackle this.
- Digital Exclusion: The absence of both legal and digital identity excludes vast populations from accessing essential services: finance, health, education, and government.
- User Disempowerment: Individuals lack transparency and real control over personal data collection, sharing and storage, eroding trust and autonomy.
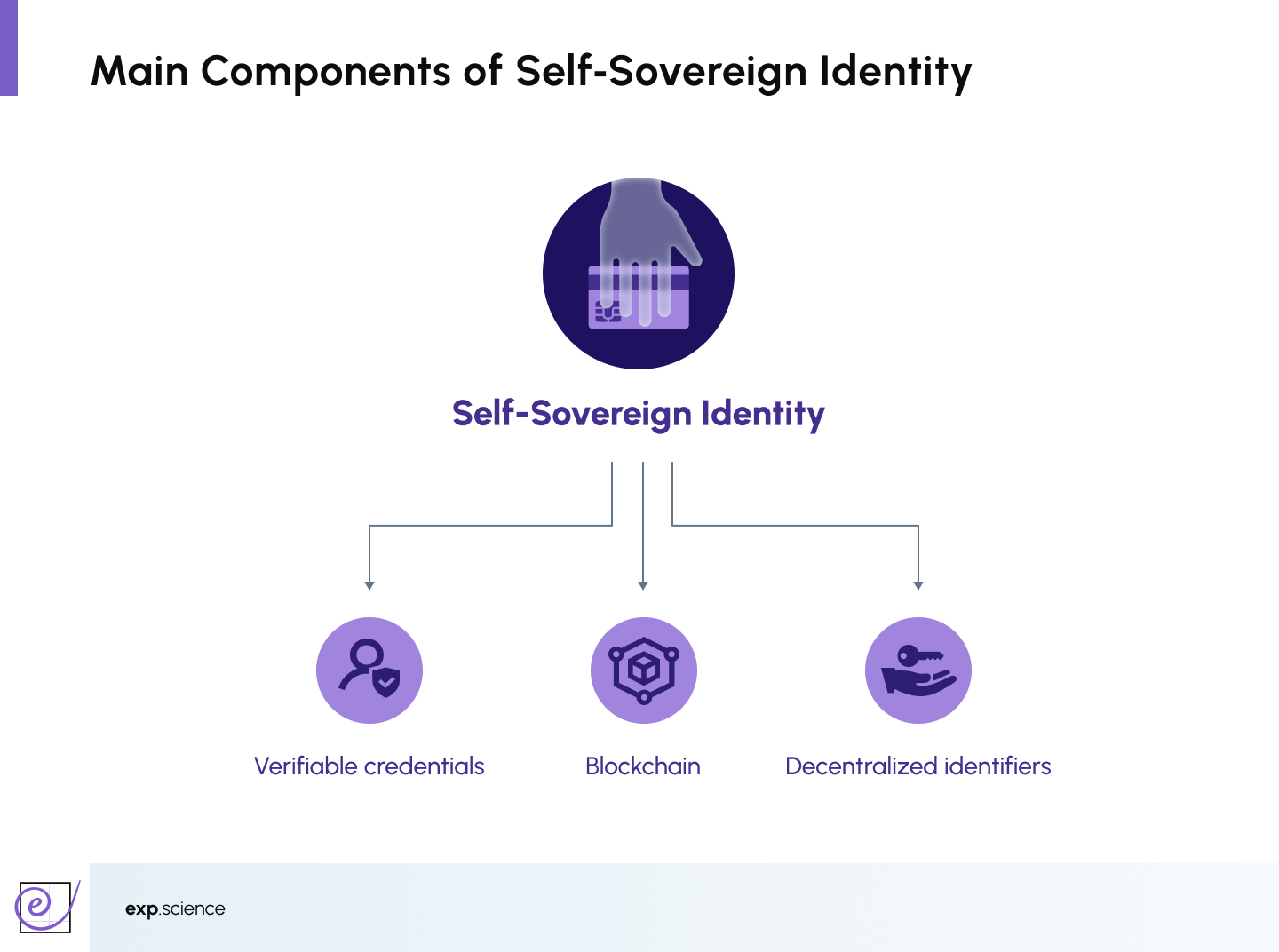
The Case for Decentralisation: Enter Self-Sovereign Identity (SSI)
Self‑Sovereign Identity (SSI) flips the paradigm: ownership and control are returned to individuals. Under SSI, users hold their credentials in secure digital wallets and reveal only the necessary attributes through cryptographic proofs; no central broker is needed.
- Decentralised Identifiers (DIDs): Unique, user-controlled IDs independent of central issuing authorities. These replace usernames or government numbers with privacy-preserving identifiers.
- Verifiable Credentials (VCs): Digitally signed claims (e.g., diplomas, licences) that are cryptographically secure and can be verified without exposing unnecessary data.
- Blockchain: Distributed ledger that ensures credentials are tamper-proof and verifiable. It removes the need for a central authority to manage identity records, providing a trusted and transparent foundation for digital identity systems.
Many privacy-preserving SSI systems also implement Zero-Knowledge Proofs (ZKPs), cryptographic techniques allowing users to verify attributes (such as age or qualifications) without revealing the underlying personal data.
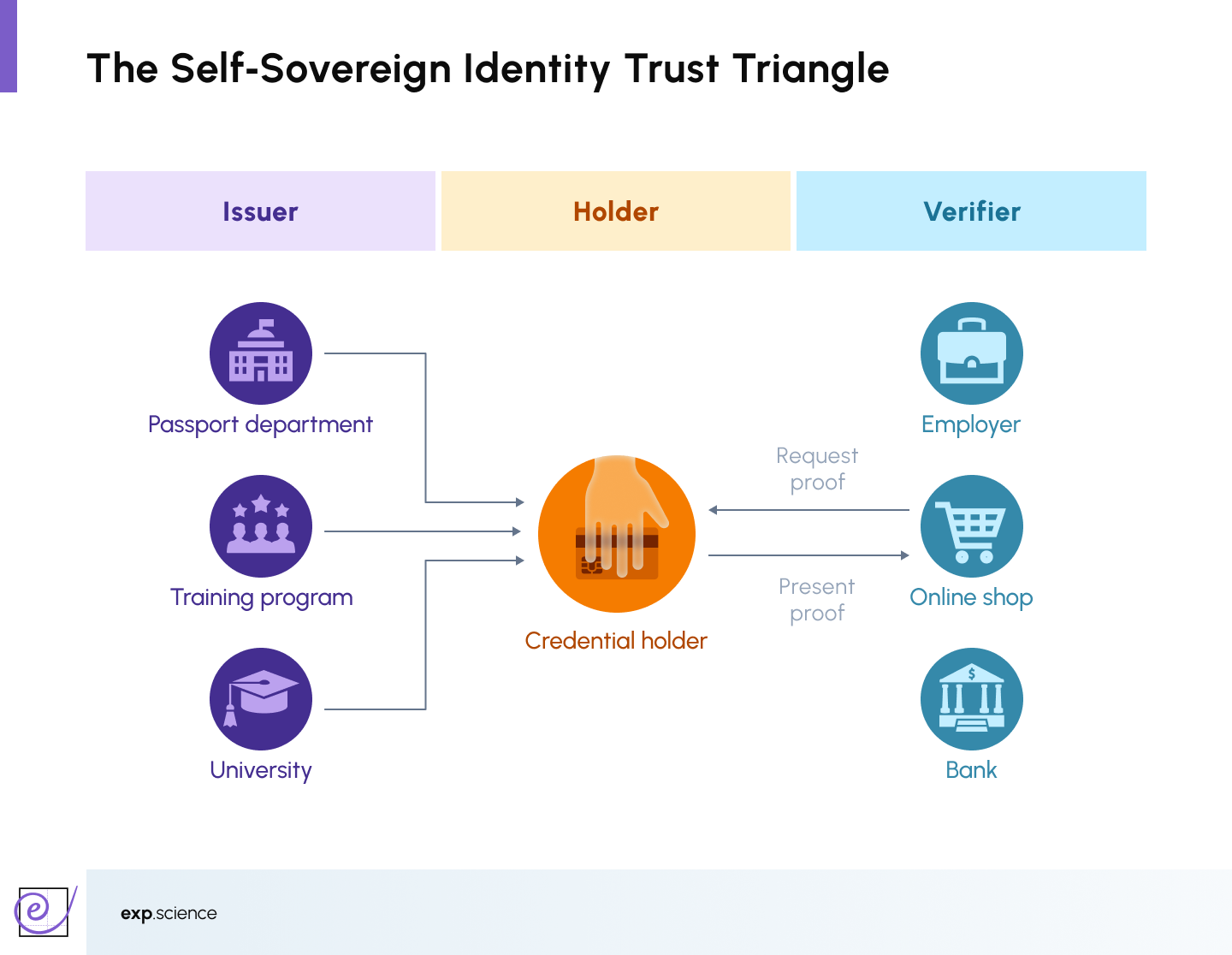
Let’s consider an example to explain how SSI works:
- A student receives a digitally signed diploma issued by a trusted entity, the University.
- This credential is stored in their digital wallet.
- When applying for a job, they use a wallet to share a cryptographic proof of the diploma with the employer.
- The employer verifies the credential's authenticity without contacting the issuer directly.
This model follows the SSI ‘trust triangle,’ where trusted issuers (passport office, university) provide credentials to holders, who store them securely. When needed, the holders can then selectively present proof to verifiers (employer, bank,) enabling secure, privacy-aware transactions without revealing unnecessary personal data.
Digital Identity and Web3: The Trust Layer
Web3 ecosystems are increasingly integrating SSI to establish trust in decentralised settings, where users are often pseudonymous. These systems bolster governance in DeFi and DAOs by combating sybil attacks (where one entity controls multiple identities to manipulate mechanisms), while facilitating secure and privacy-respecting access to services, without sacrificing anonymity.
A standout initiative is Hedera’s decentralised identity infrastructure, which supports the SSI model at scale:
- Decentralised Identity (DID) Service allows developers to manage DID lifecycles -creating, verifying and revoking credentials- following the W3C DID and VC standards via the Hedera Consensus Service (HCS).
- It uses cryptographic credentials recorded with consensus timestamps, enabling high-throughput, tamper-evident identity proofs suitable for applications in supply chains, IoT, finance and more.
- With SDK support (JS/Java/Python plugins), developers can integrate identity issuance and verification directly into their applications, ensuring privacy-preserving, user-held credentials anchored securely on Hedera.
Using Hedera as a trust layer, developers can:
- Issue credentials (e.g., university degrees, professional certifications) to users.
- Anchor the credential metadata via HCS for future verification.
- Enable users to present credentials privately, while verifiers check authenticity using the hash anchored on Hedera.
This model decentralises identity without sacrificing scalability or security; no central intermediaries, just cryptographic guarantees and interoperable standards.
These kinds of tools represent a shift towards community-driven, verifiable identity without requiring centralised platforms. They enable novel use cases in Web3 communities, from trust-based reputation systems that evaluate users based on past actions or peer validation, to quadratic funding, a method that enables democratic resource distribution in decentralised communities by amplifying smaller contributions from any users.
The Biometrics Debate: Ethical Identity in Web3
A notable but controversial Web3 identity initiative is Worldcoin, which employs an orb device to capture iris scans to establish proof of personhood via token incentives, where users receive a unique ID. While the project aims to provide global access to identity and currency, it raises ethical and privacy concerns:
- European regulators ordered the deletion of biometric data from 400,000 scans in Spain due to GDPR concerns.
- Privacy advocacy groups, including EPIC, warn that scanners may disproportionately affect vulnerable populations.
- The Portuguese data watchdog (CNPD) flagged inadequacies in consent procedures, particularly for minors.
- Registration uptake remains low relative to projections, with 12 million users compared to the claimed target of 50 million.
This initiative sparks a broader debate: can biometrics be ethically deployed? Are individuals fully informed? How can long-term consent and data governance be assured? The case of Worldcoin highlights the ongoing tension between technological advancement and individual rights in identity architecture.
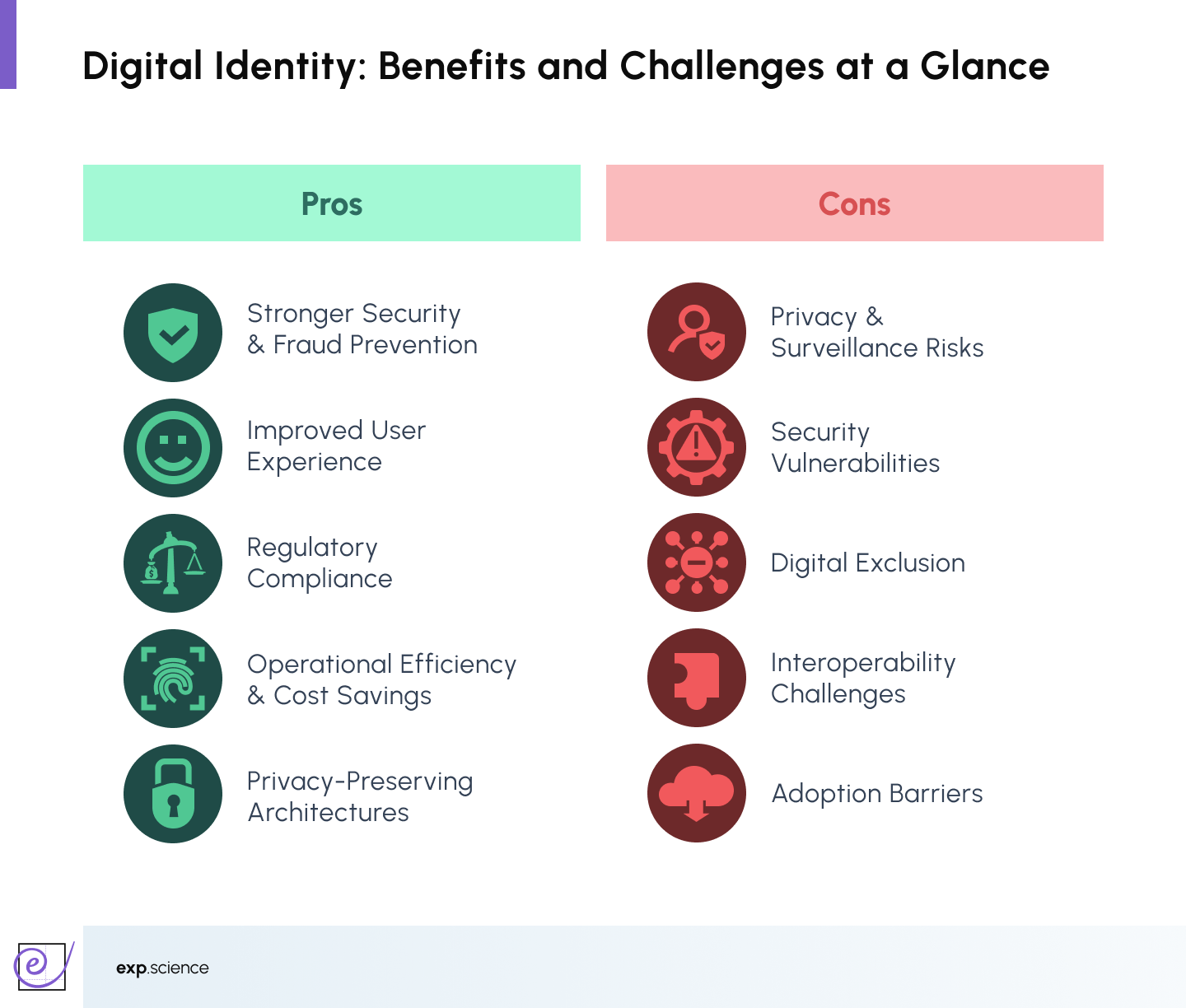
Pros and Cons of Digital Identity Systems
As digital identity evolves, from biometrics and single sign-on (SSO) to decentralised identifiers and verifiable credentials, the benefits and risks are becoming clearer. Digital identity architecture involves trade-offs between usability, privacy, and security, and as a rapidly changing technology that offers a radically new approach, the landscape is continuously shifting, requiring ongoing adaptation and trust-building.
Benefits
- Stronger Security & Fraud Prevention: Biometric verification, multi-factor authentication (MFA), and cryptographically verified credentials reduce identity fraud and impersonation attacks.
- Improved User Experience: Seamless, mobile-friendly onboarding and reusable credentials simplify access across services, reducing user friction.
- Regulatory Compliance: Digital identity systems help organisations meet KYC, AML, and GDPR requirements through automated verification and data minimisation.
- Operational Efficiency and Cost Savings: Reusable digital credentials reduce onboarding time and verification costs across sectors.
- Privacy-Preserving Architectures: Blockchain anchoring and selective disclosure mechanisms (e.g., DID/VC) provide users with greater control over their data.
Challenges & Risks
- Privacy & Surveillance Risks: Poorly governed or centralised systems can enable mass surveillance or unauthorised data profiling.
- Security Vulnerabilities: Complex integrations or legacy systems can introduce new attack surfaces and risks.
- Digital Exclusion: People without access to digital devices or lacking digital literacy may be left behind.
- Interoperability Challenges: Fragmented standards and siloed implementations still hinder cross-platform identity flows.
- Adoption Barriers: Shifting away from entrenched legacy systems requires significant coordination, investment and trust-building.
These dynamics make identity transformation a multi-faceted issue encompassing technology, policy, infrastructure and social equity.
Real-World Applications of Digital Identity
Beyond the risks and challenges, digital identity systems are already transforming our daily interactions across industries.
- Finance: Banks use digital KYC processes based on verified credentials to comply with AML regulations.
- Healthcare: Patients control and share their medical records securely using platforms like MyData.
- Education: Universities issue digital diplomas that employers can instantly verify, such as via Learning Machine (Hyland).
- Governance: Estonia’s e-ID, which supports e‑voting and healthcare access, and India’s Aadhaar systems have shown different trade-offs. Estonia prioritises privacy-by-design; Aadhaar demonstrates scale but raises surveillance concerns.
- Web3: Hedera integrates DIDs and VCs to enable secure, privacy-preserving authentication, supporting SSI models and scalable Web3 applications.
Global Trends In Digital Identity Infrastructure
A growing convergence among public, private, and open-source initiatives is working towards more interoperable and user-centric digital identity systems worldwide. Building this future infrastructure will require clear standards (such as W3C DID/VC), harmonised regulations, user literacy programmes, and strong public trust frameworks.
Key initiatives illustrating this global momentum include:
- UNDP’s Digital Public Infrastructure (DPI): Advocates for open-source, inclusive digital identity platforms.
- World Bank ID4D Programme: Supports digital ID implementation in over 50 countries.
- European Digital Identity Framework (eIDAS 2.0): Aims to deliver interoperable digital wallets across member states.
Overall, digital identity transcends technical innovation, becoming a question of dignity, autonomy and civic participation. As digital services pervade every aspect of life, ensuring that everyone can prove their identity securely, privately and under their personal control is essential for fairness in the digital era.
The age of centralised control over identity is being increasingly challenged. In its place, decentralised, user-centric models are emerging as more secure, privacy-preserving, and inclusive alternatives, but the new model still needs to overcome its flaws and setbacks before fully challenging the established ways.


.jpg)


%20(1).jpg)
.jpg)

